“Now What?!”
At this point Mary’s web server had been down for over a week. I knew that we had a DDOS attack of some sort but I didn’t know what to do. After looking at this post in the InterServer Forums I got some ideas.
https://forum.interserver.net/forum/threads/interserver-have-ddos-flood-protection.1872/
Basically you have a few options.
1) You can detect incoming bad guys and null route them. This means that their IP is blocked from future accesses to your server. This would be good if the Attacks were not distributed. I.E. they were coming from a few hosts. However, I tried to null route using a shell script and got to over 700 bad Ips with no end in site. And eventually the system locked up.
2) You can a more efficient server. Quags the Admin recommended using nginx and a more efficient firewall. I configured and ran nginx but this didn’t work for me.
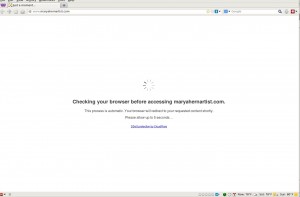
3) You can get external help ie. Use a reverse proxy. Quags recommended www.cloudflare.com. Since I was at the end of my rope I decided to use them. Turns out they have a free package. (If it’s free then it’s for me!). You can set the cloudflare Security Settings to “I’m under a DDOS attack”. I also had to set my firewall to reject all Ips except those from cloudflare. Then miraculously the website started functioning. However, each visitor got this interstitial page:
I ran a short survey on Facebook to see if this 5 second delay was a show stopper: Yes it seemed that for some it indeed was a show stopper. I would also suspect that most casual web users would see this and bypass it and go somewhere else. My facebook friends were warned that there was a 5 second delay so they were more understanding than the average user.
Somehow I stumbled upon a security module for Apache. It is called strangely enough mod_security. It is a snap to install .
yum install mod_security <cr>
yum install mod_security_crs <cr>
Be aware that mod_security by itself does no work. You need the filters. They live in
/etc/httpd/modsecurity.d/activated_rules/
I used all the filters except the one for sql injection. And then I turned the security setting in cloudflare from “I’m under attack” to “high”. Voilla Now the site “just works.” Oh boy!
So what did I learn.
1) You can solve at least some DDOS issues for no $$$. So far the solution costs me $.01. Next month it will be $6.00 less than what I originally paid.
2) Shared hosting seems useless for DDOS attacks. I had to change firewall and Apache settings. I don’t see how this would work in a shared environment.
3) You have to monitor your hosting provider to see if they changed their policies for the worse. Apparently mine did.